Go Language - RSA Encryption And Decryption Example
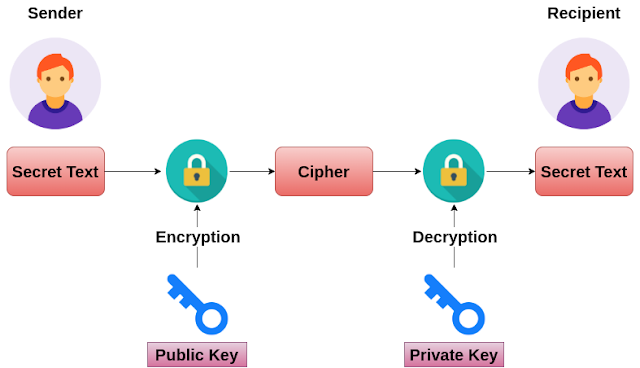
The RSA algorithm (Rivest-Shamir-Adleman) is a cryptographic algorithm that is used for specific security services or purposes, which enables public-key encryption and is widely used to secure sensitive data, particularly when it is being sent over an insecure network such as the HTTP. A public key is shared publicly, while a private key is secret and must not be shared with anyone. The following illustration highlights how asymmetric cryptography works: Example 1: RSA Encryption and Decryption with OAEP, package main //Required imports for Encryption & Decryption import ( "crypto/rand" "crypto/rsa" "crypto/sha512" "encoding/base64" "fmt" ) func main() { //3072 is the number of bits for RSA bitSize := 3072 //Generate RSA keys privateKey, err := rsa. GenerateKey(rand.Reader, bitSize) if err != nil { panic(err) } publicKey := privateKey.PublicKey //Your secret te...